Google Phishing Scam Affects One Million
May 11, 2017
On May 3, a new phishing scheme made the rounds through Google emails, with users who clicked through sharing their contact list with the scammers.
The subject line was not identical to what a real shared document email would look like, nor was the content of the email; however, the “View in Docs” button was, and many clicked on it without thinking anything of it. This brought them to an actual Google login page, where they were asked to sign in and grant “Google Docs” permissions to their account data. From here, the phishers had access to their contacts to send out more fake emails.
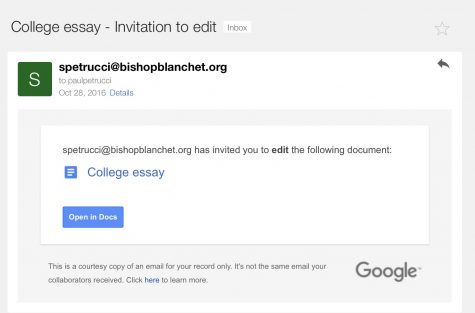
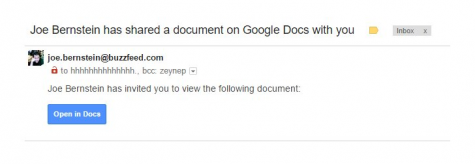
This is not a new scam, as it has happened before in the form of attached PDF’s and other seemingly-normal emails. The new aspect is that it used a real Google login page to trick people into granting admission to a third-party app simply named “Google Docs,” which meant it lacked many tell-tale hints of a phishing scam.
“While contact information was accessed and used by the campaign, our investigations show that no other data was exposed,” said Google in a statement.
They are still looking into who perpetrated this.
The scam was shut down by Google within an hour, but not without impacting about a million accounts. No student at Blanchet, however, was affected.
“There are safeguards in place [for Blanchet email addresses] that should filter the majority of dangerous emails out,” said Philip Hodgins. “We try to keep our email as secure as possible.”
While this specific scheme has been resolved, students should still make sure to practice smart email habits. These include not opening anything sent to them by unknown contacts or “Docs” emails that doesn’t follow the right format, checking the link on any Google login page to make sure it is legitimate and starts with “http,” and using common sense when deciding what permissions to allow to third-party apps.





